What is facial recognition? Explaining how it works, the differences with facial recognition, benefits, examples, and points to note!

Facial recognition is one of the biometric authentication technologies that realize improved security and operational efficiency. Its use is progressing in various scenes, from unlocking smartphones to access management in offices and boarding procedures at airports.
In this article, along with an overview of the basic mechanism of facial recognition and the difference from face recognition, we will explain in an easy-to-understand and comprehensive manner everything from specific implementation cases and benefits of introduction to points to note when implementing.
It is packed with content that shows how facial recognition technology is useful in business scenes and provides hints for considering the introduction of the latest facial recognition systems, such as AI-powered or cloud-based types.
Nextremer offers data annotation services to achieve highly accurate AI models. If you are considering outsourcing annotation, free consultation is available. Please feel free to contact us.
|
【Table of Contents】 |
1. What is Facial Recognition?

Facial recognition is a type of image recognition technology used to detect a face from images or videos acquired by a camera and authenticate a specific individual. It is realized through a combination of image recognition by AI and image processing technology, performing identity verification based on individual facial features such as eyes, nose, and mouth.
Facial recognition systems are utilized in situations where security is required, as listed below.
|
By using a facial recognition system, smoother and safer identity verification is possible compared to traditional authentication means such as passwords and ID cards. Therefore, it is recognized as a tool that balances convenience and safety.
The Difference Between Facial Recognition and Face Recognition
Facial recognition and face recognition basically use the same technology, but there are clear differences in their purpose, application, and required precision.
"Facial recognition" (authentication) aims for personal identity verification and is a technology that performs 1-to-1 matching. In other words, it determines if a person is who they claim to be by matching input face images against registered face data.
Main application examples include situations where identity verification is required, such as unlocking smartphones or managing entry/exit in office buildings. Since it is used to specify identity, high precision and data security are required.
On the other hand, "face recognition" (identification) aims for the identification or classification of unknown persons and is a technology that performs 1-to-many identification. It identifies face data with a high match rate by matching an input face image against a vast database.
Application examples include narrowing down suspects in criminal investigations, helping to identify unknown individuals. In face recognition, it is often acceptable to present multiple candidates. Therefore, relatively lower precision may be sufficient in some cases.
Basic Mechanism
In facial recognition systems, technology from the field of image classification is particularly utilized within image recognition AI.
Face authentication is performed through several processes as follows.
|
First, the facial recognition system detects an individual's face from footage or images acquired by a camera. In this process, Convolutional Neural Networks (CNN) are often used.
A CNN is a neural network architecture designed to efficiently extract image features such as the arrangement of facial parts.
Next, facial feature data such as eye positions and the shape of the nose and mouth detected by the CNN are extracted, encrypted, and saved.
Then, at the time of authentication, the AI matches newly acquired face data from the camera with the saved encrypted data. During matching, the AI enhances the precision of identity verification by classifying the degree of facial match and evaluating reliability.
In this way, by utilizing AI from face detection to feature extraction and data matching, facial recognition systems achieve high precision and safety.
Types of System Configuration
The configuration of facial recognition systems is broadly divided into the following two types: the edge method and the cloud method.
| System Configuration Type | Edge Method | Cloud Method |
| Mechanism | Equipping the edge device with the facial recognition system | Processing camera footage in the cloud |
| Benefits |
|
No need for large-scale edge device implementation |
| Drawbacks | Installation of edge devices is required |
|
2. Benefits that Implementing Facial Recognition Brings to Companies
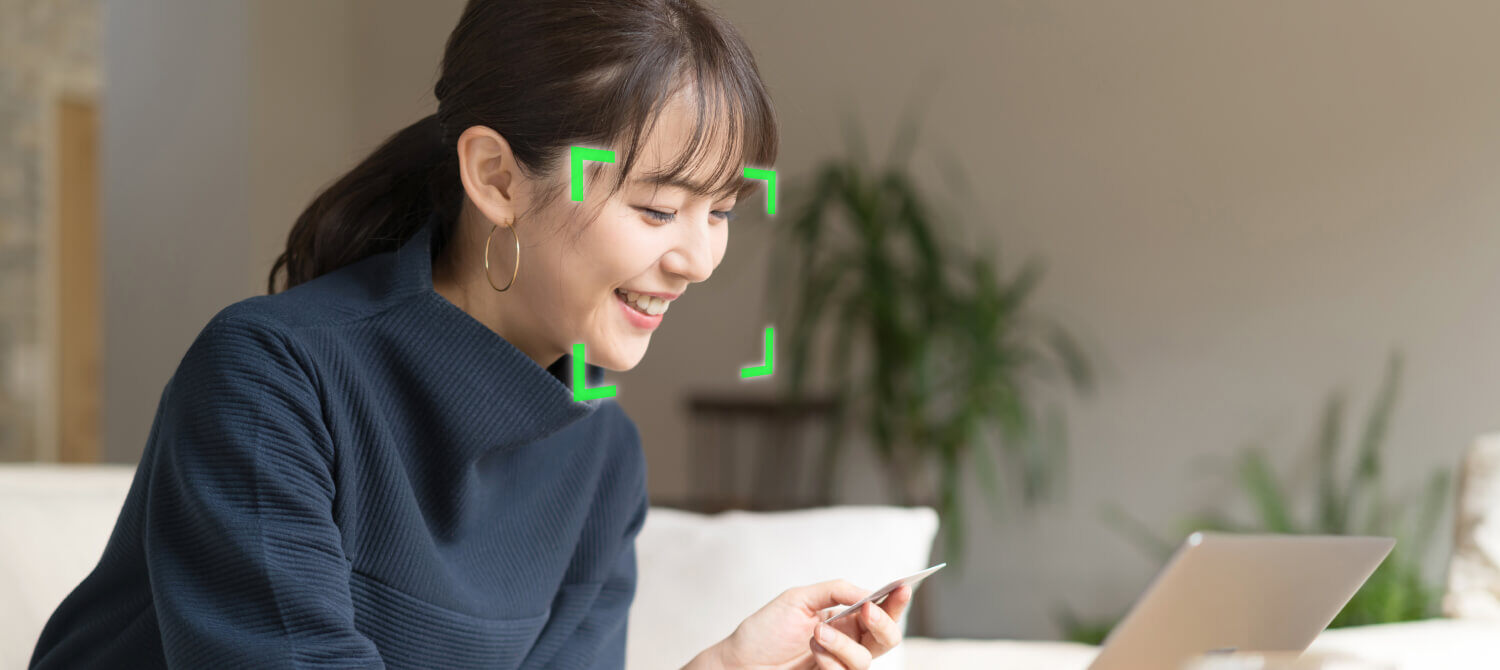
Facial recognition brings many benefits to companies in terms of security and efficiency. Below, we introduce the specific benefits that facial recognition brings to companies.
Ability to Establish High Security
Facial recognition provides a higher level of security compared to other authentication means. This is because faces have unique individual characteristics, and facial recognition systems require detailed facial feature data.
The probability of another person having the same face is extremely low, and the risk of spoofing can be significantly reduced compared to passwords and PIN codes.
Also, unlike IC cards and passwords, loss, theft, or user forgetfulness does not occur. Therefore, the risk of double issuance or leakage of cards and passwords drops significantly.
Furthermore, security can be strengthened even further by combining facial recognition with other authentication means such as fingerprint authentication or passwords for use as "multi-factor authentication." Through a multi-layered authentication process, robust protection is possible while minimizing security risks.
Improvement of User Convenience
With facial recognition, passage is easily possible even when a user's hands are full. For example, even when carrying luggage with both hands, authentication is completed simply by presenting one's face without having to take out an authentication card.
Also, in general, recognition speed is often faster compared to traditional authentication means such as IC cards, and it is possible to reduce waiting times when large numbers of people move in offices or event venues.
Therefore, by implementing a facial recognition system, smooth movement and unlocking become possible, leading to improved user convenience.
Streamlining Access Management
Since facial recognition is performed through a camera, no special operations or guidance on the security staff's part are necessary, and authentication can be done in a short time. Through this non-contact authentication system, identity verification is possible more efficiently compared to physical keys, ID cards, or fingerprint authentication.
Also, by building a mechanism where only employees or users who have pre-registered their face data can enter and exit, access management is automated. This allows for reduced management costs and can significantly improve operational efficiency.
Due to these characteristics, its use is progressing particularly in places with heavy foot traffic for entry/exit management or in situations where rapid authentication during payment is required.
3. Implementation Case Studies of Facial Recognition Systems

Facial recognition systems are actually utilized in various companies. Below, we introduce application examples of facial recognition systems.
Realizing Walk-through Access Management (Petrochemical Company in Taiwan)
In a new headquarters building completed in Taipei by a major Taiwanese petrochemical company, it was expected that more than 5,000 employees would enter and exit daily across multiple wings. With traditional access management using card readers, there was a possibility that a large number of employees would wait in lines depending on the time of day, making efficient access control a challenge.
Therefore, they introduced a CyberLink access control system incorporating high-precision facial recognition technology.
Since this system can authenticate with high precision even at an angle, from a distance, or while walking, walk-through access management is possible.
Its introduction is contributing significantly to the improvement of employee convenience and operational efficiency.
Reference: https://jp.cyberlink.com/faceme/insights/cases/1143/petroleum-industry-access-control-time-attendance-faceme-facial-recognition
Contributing to Monitoring Functions in Senior Residences (Mitsui Fudosan Residential)
As a first-of-its-kind attempt in Japan, Mitsui Fudosan Residential implemented a facial recognition system for entrance doors and common facilities in all 340 units of its senior residence, "Park Wellstate Nishiazabu." Through this system, residents can move stress-free using facial recognition, improving convenience and safety.
Provided by NEC, this facial recognition system was implemented in common facilities such as the entrance and pool in addition to each unit, allowing residents not only to go out without a key but also to move smoothly within the building. This frees residents from worries about losing or misplacing keys and from troublesome operations while carrying luggage.
Furthermore, it enables identification of those staying for long periods in specific locations such as large public baths and coordination with safety confirmation systems, realizing monitoring functions for residents that were difficult with traditional key systems.
Reference: https://jpn.nec.com/press/202407/20240729_01.html
Promoting Store Visits with a Digital Stamp Rally (ANA Trading Co., Ltd.)
ANA Trading Co., Ltd. introduced an easy-to-participate facial recognition stamp rally service so that passengers boarding planes can more easily stop by ANA FESTA on both their outbound and return trips.
This facial recognition stamp rally service adopts Panasonic's facial recognition technology and Hitachi's biometric authentication integrated infrastructure service equipped with PBI.
The stamp rally service works by pre-registering face information on a smartphone and linking it with the ANA Mileage Club passenger number. In doing so, it is a mechanism that can be easily used at stores with just facial recognition without taking out a card or smartphone.
Face information is encrypted and saved in a form that cannot be restored, and it is built to satisfy the high security standards of the ANA Group.
Since its introduction, user participation has been strong, achieving the initial target value early on and receiving a response large enough for upward revisions. The ability to use it with peace of mind due to high authentication precision and the ease of participation in the facial recognition stamp rally are contributing significantly to promoting store visits.
Reference: https://connect.panasonic.com/jp-ja/case-studies/anagroup
4. Points to Note When Implementing a Facial Recognition System

While facial recognition systems are convenient, there are several points to note when implementing them. Below, we introduce matters that require particular attention.
Privacy Protection of Face Data
Since face data falls under personal information, extreme care is required in its handling. In particular, when acquiring data, it is required to clarify the purpose of use and notify the individual.
Only after establishing a privacy policy is an environment prepared where users understand how their data is used and can use the facial recognition system with peace of mind.
Also, technical security measures such as encryption and anonymization of face data are important. By thoroughly implementing these measures, it becomes possible to ensure privacy protection and minimize the risk of data leakage.
To balance the convenience of facial recognition technology with privacy, companies are required to formulate and operate strict data protection policies.
High-Quality Training Data is Necessary
To enhance the precision of facial recognition systems, high-quality training data is necessary. This is because using low-quality data lowers authentication precision and increases the risk of misidentification and authentication errors.
Therefore, it is necessary to gather diverse data so that stable performance can be exhibited even under specific conditions, such as when wearing a mask or in places where brightness changes extremely.
Also, it is important to apply accurate image annotation—that is, assigning correct labels—to the data registered in the system. By using appropriately annotated data, the AI can accurately learn facial features, improving authentication precision.
By ensuring the quality of training data, it becomes possible to provide a safe and comfortable authentication system for users, leading to improved satisfaction.
Nextremer offers data annotation services to achieve highly accurate AI models. If you are considering outsourcing annotation, free consultation is available. Please feel free to contact us.
Establishing the Usage Environment
The precision of facial recognition systems is affected by external factors such as lighting conditions and weather. Therefore, upon system implementation, it is important to carefully consider the installation location, taking into account the impact of environmental factors on authentication precision.
For example, when installing outdoors, ingenuity is required to avoid the effects of direct sunlight, rain, and wind. Also, even indoors, environments where the intensity or angle of lighting changes significantly depending on the time of day can lead to decreased system performance.
By optimizing the usage environment, the precision of the facial recognition system increases, leading to smooth operation.
Complying with Legal Regulations
In implementing a facial recognition system, it is necessary to follow relevant laws and regulations such as the Act on the Protection of Personal Information. Since face data is handled as personal information, appropriate procedures based on the law are required for its collection and use.
In particular, for the collection of face data, it is important to clarify the purpose of use and obtain the individual's consent. When handling employee facial recognition data, compliance with laws such as the Labor Standards Act and the Industrial Safety and Health Act also becomes necessary.
Furthermore, high security standards are required for data storage and management, necessitating measures to prevent information leakage and unauthorized use.
Please also see this article regarding points to note concerning data collection.
"Things to keep in mind when requesting annotation data collection"
Anti-Spoofing Measures
In recent years, along with the progress of AI technology, deepfake technology has also evolved rapidly, and damage from spoofing using images that look exactly like the actual person is increasing. Serious risks are concerned for spoofing, such as unauthorized access to confidential information, fraudulent execution of financial transactions, and unauthorized entry into physical security zones.
To address such risks, the introduction of multi-modal authentication and the utilization of 3D facial recognition technology are effective.
In multi-modal authentication, by combining not only facial recognition but also other biometric authentication such as fingerprints and iris, authentication precision can be further enhanced and the risk of unauthorized access can be reduced.
Also, through three-dimensional recognition using 3D depth sensors, spoofing by deepfakes, which is difficult to judge with 2D images, can be prevented.
5. Summary
The introduction of facial recognition technology not only strengthens security but also enables non-contact and rapid identity verification, contributing significantly to improved employee efficiency and customer experience.
Also, facial recognition technology is indispensable for realizing improved internal operational efficiency and strengthened security of provided services. By implementing a facial recognition system capable of handling diverse environments, a highly reliable security foundation essential for companies can be built. It can be said to be an important step for providing an environment that customers and employees alike can use with peace of mind.
Nextremer offers data annotation services to achieve highly accurate AI models. If you are considering outsourcing annotation, free consultation is available. Please feel free to contact us.
Author
Toshiyuki Kita
Nextremer VP of Engineering
After graduating from the Graduate School of Science at Tohoku University in 2013, he joined Mitsui Knowledge Industry Co., Ltd. As an engineer in the SI and R&D departments, he was involved in time series forecasting, data analysis, and machine learning. Since 2017, he has been involved in system development for a wide range of industries and scales as a machine learning engineer at a group company of a major manufacturer. Since 2019, he has been in his current position as manager of the R&D department, responsible for the development of machine learning systems such as image recognition and dialogue systems.
Latest Articles



